Q: SFTP Server Public Key Authentication. Quick question regarding limagito and it’s SFTP server. Is it possible to configure an ssh key instead of using user / password?
A: In version v2021.10.13 we added the possibility to use Public Key authentication with our SFTP server.
We used PuTTY Key Generator to create a Public and Private key file. Click the ‘Generate’ button and move your mouse around. Afterwards we added a passphrase and saved the public and private key to a file.
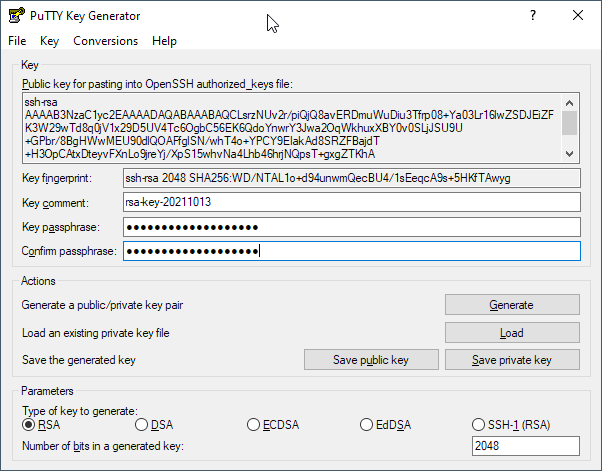
Saved .ppk files:
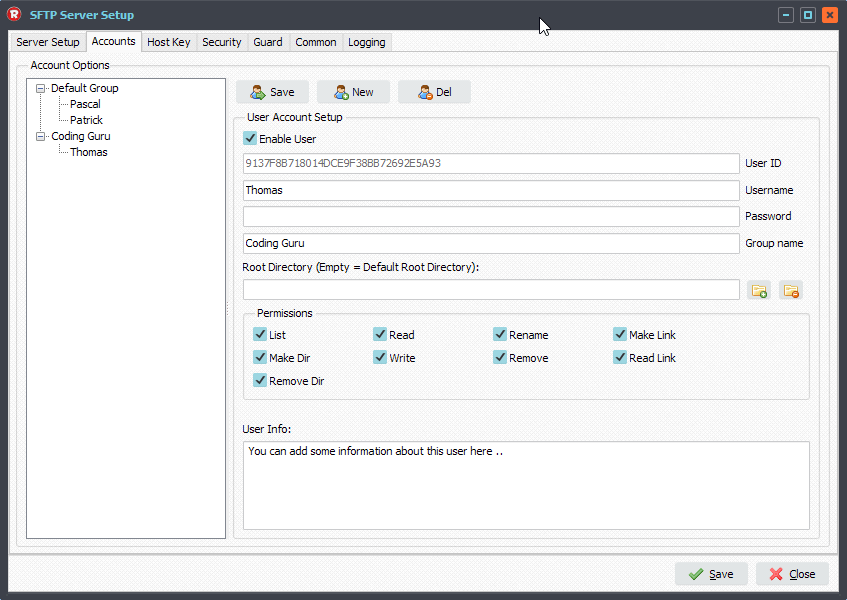
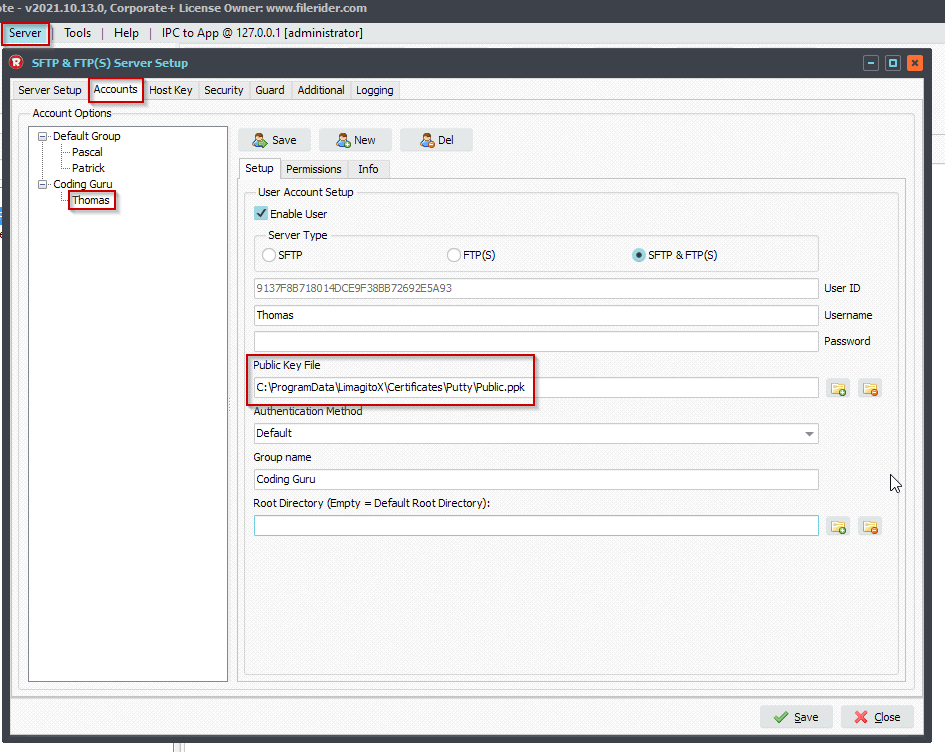
Next open the SFTP Server Setup and select the ‘Accounts’ tab. Choose the User Account which you want to add the Public Key file to. Select the Public Key File and do not forget to click the ‘Save’ button of the ‘User Account Setup’ (at the top).
Click ‘Save’ button at the bottom to close the SFTP Server Setup
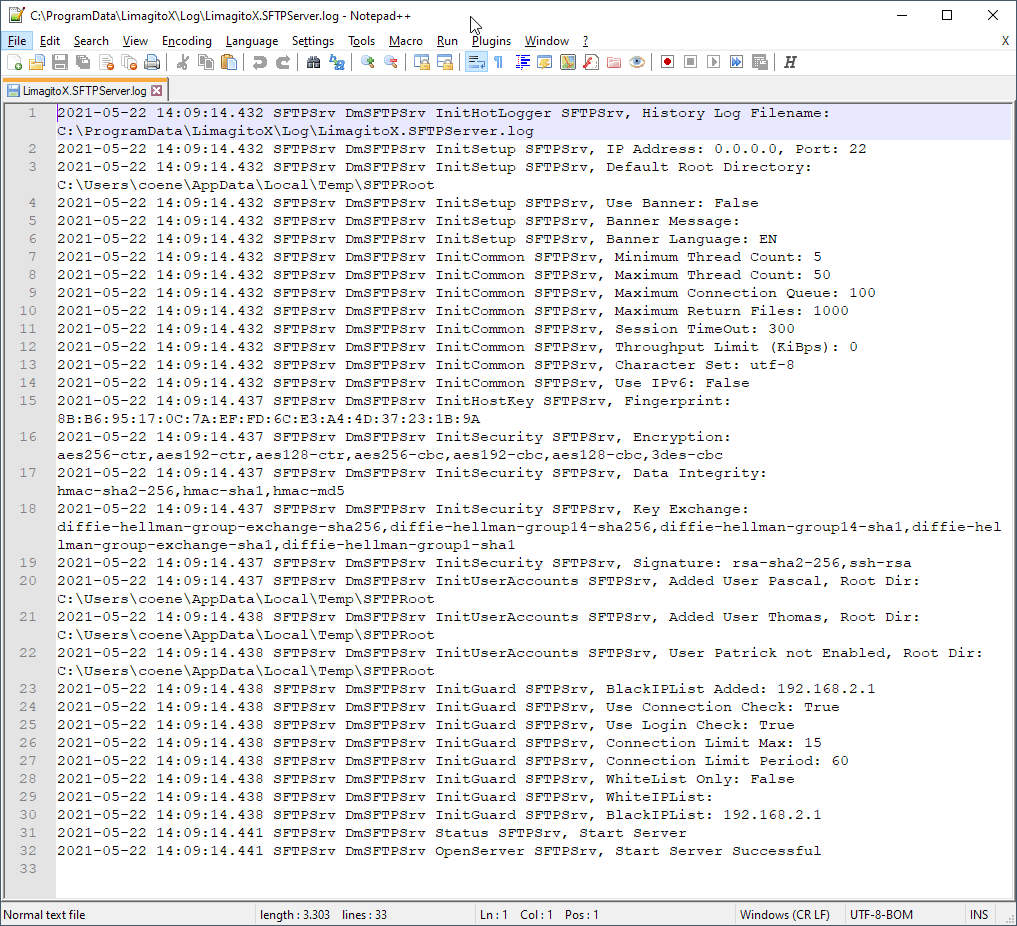
If you want to be sure that the Publice Key file was loaded correctly then you please check the SFTP server Log.
To enable logging of the SFTP Server (Logging Tab):
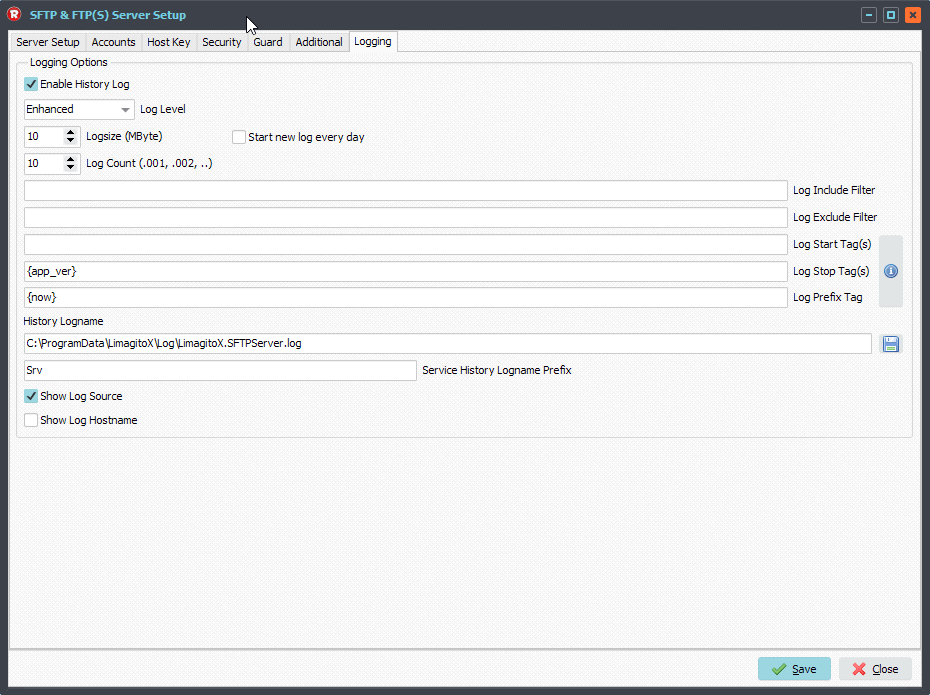
We used the default log folder. It is never ever a good idea to put a log file on a network share, please always use a local drive.
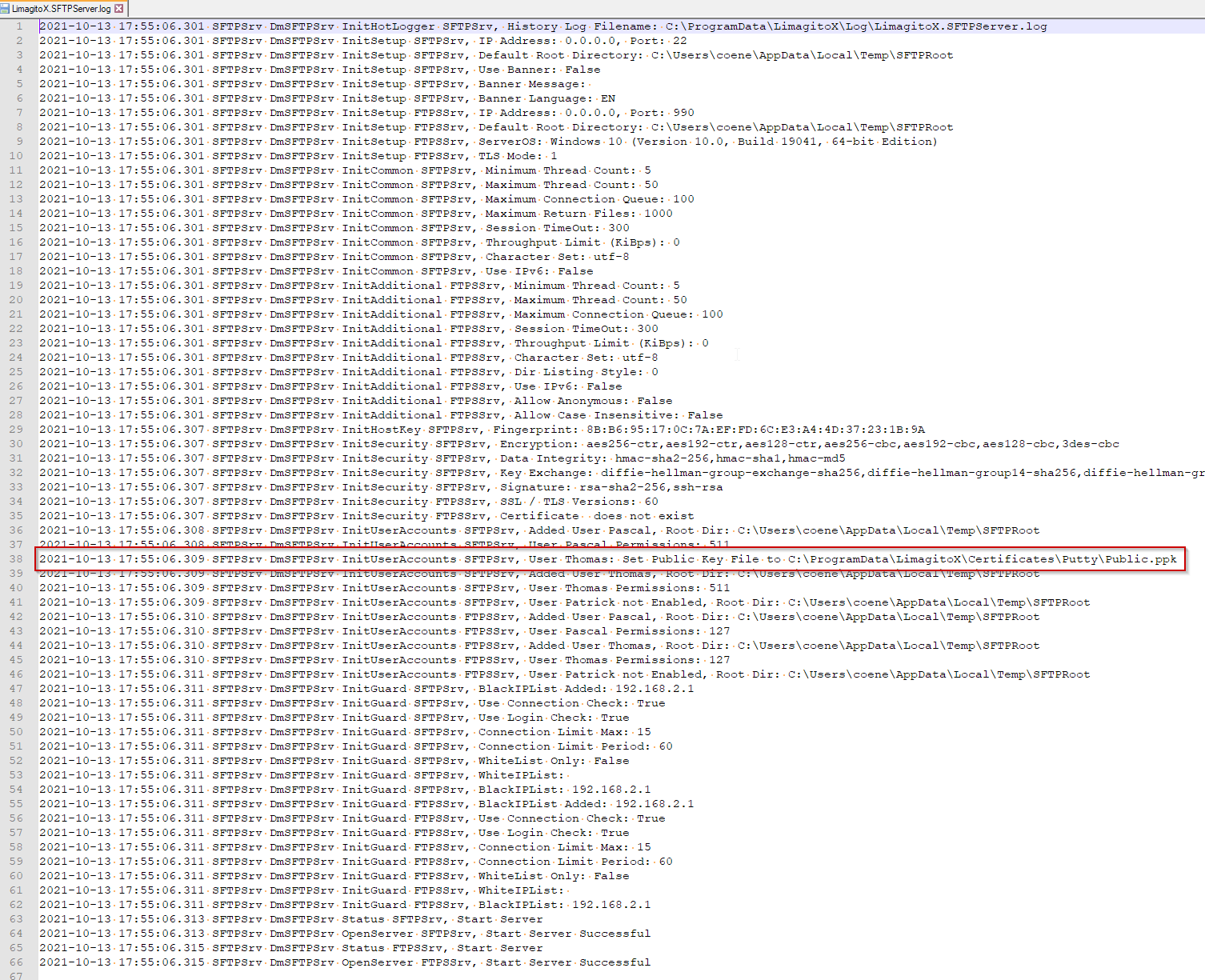
SFTP Server log content, search for ‘Public Key’. In our case no loading error, so we are good to go.
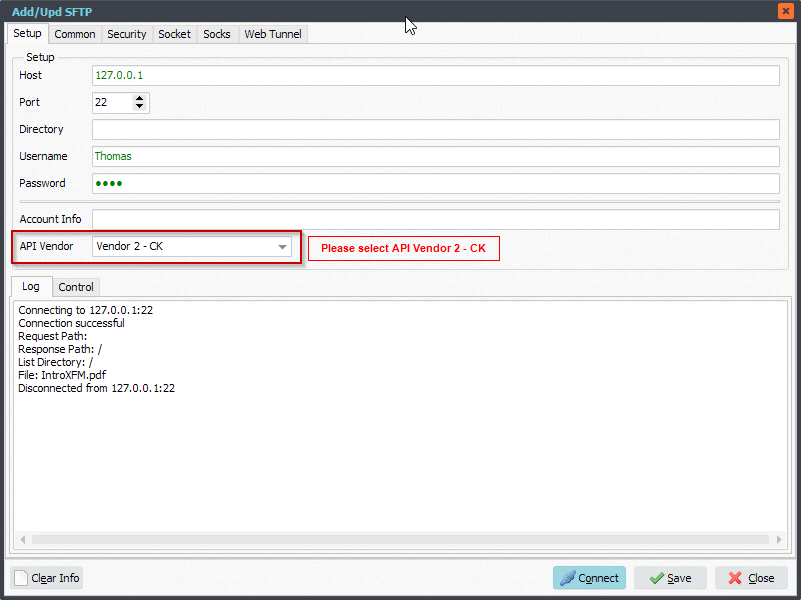
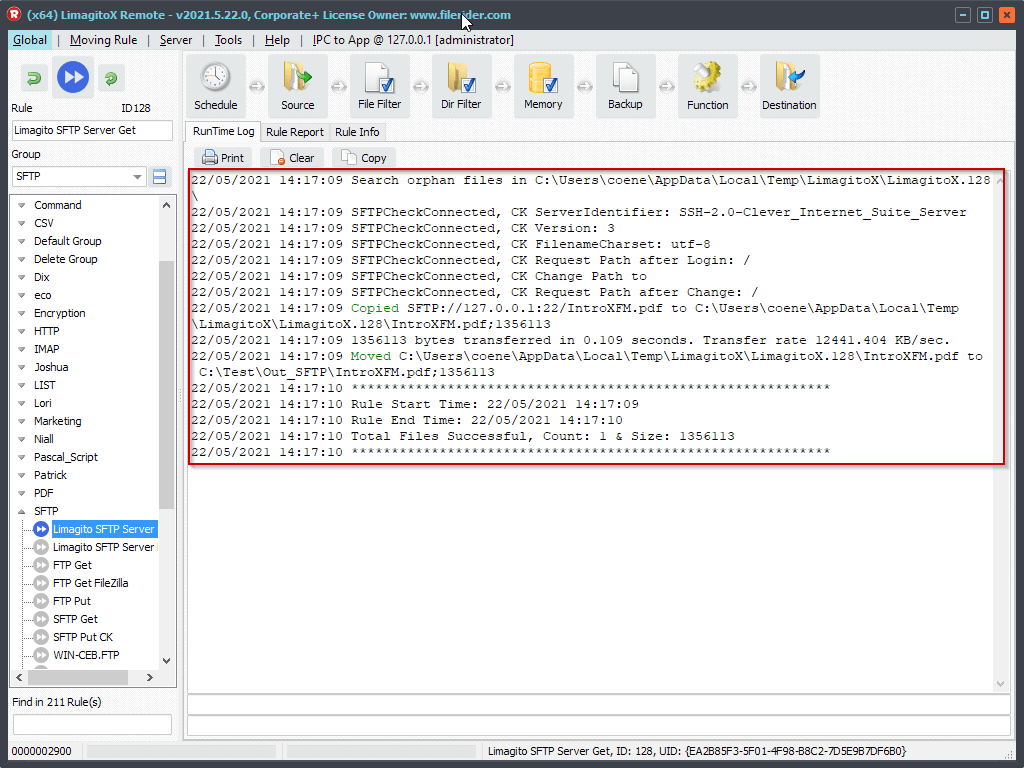
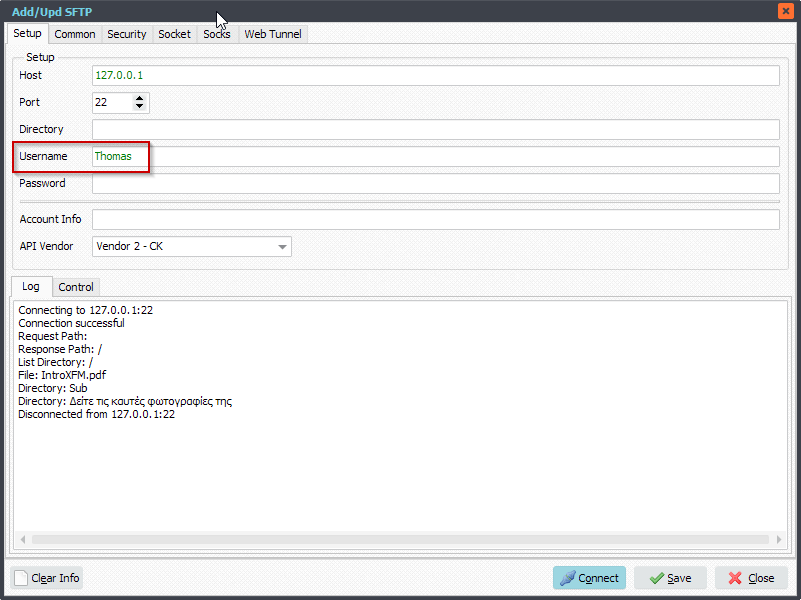
We tested the Public Key Authentication using our own File Mover. Be sure to select our second API Vendor: Vendor 2 – CK.
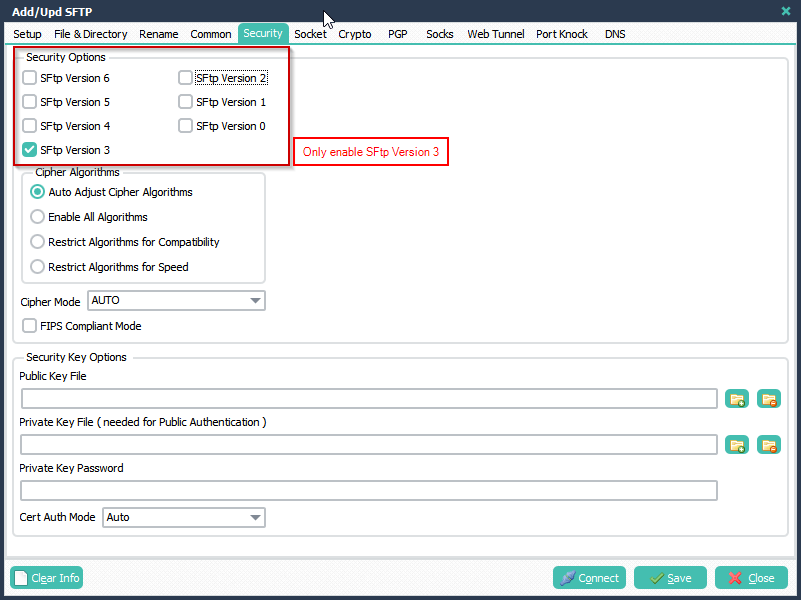
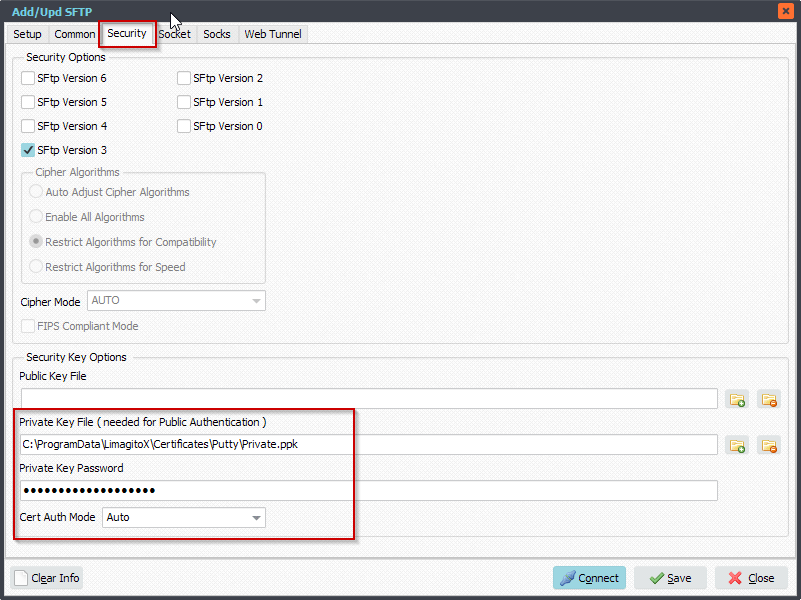
Select the ‘Security’ Tab and add your Private Key File and Private Key Password (only if you added a password/passphrase to this file).
Previous information about our SFTP server option: Limagito SFTP Server
#FileTransfer #SFTP
Best regards,
Limagito Team