FTP Destination
FTP Destination Setup
Setup Options
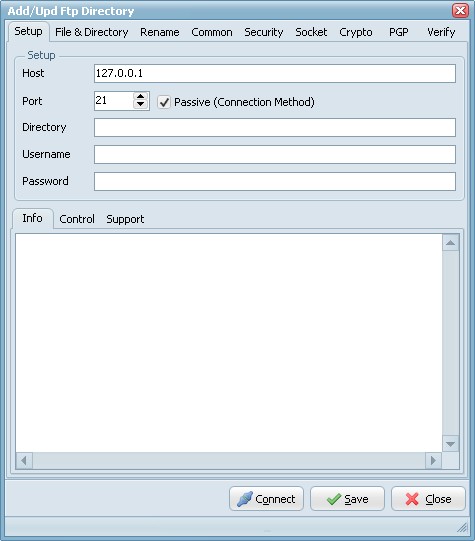
- Host: This option specifies the address of the host to connect to.
- Port: Port number on the host to connect to (Default value is 21).
- Passive: Active connections (or when Passive is disabled) indicates that the FTP server will open the connection for the data channel. In other words, the FTP client will listen for the server to open a connection for the data channel.
- Directory: Directory on the server file system.
- Username: Authentication identity used when logging in to the server (example: Anonymous).
- Password: Authentication credentials used when logging into the server.
- Connect: Check connection setup.
File & Directory Options
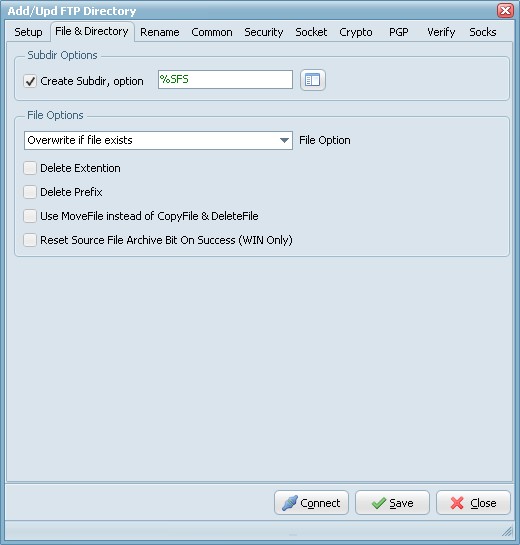
Subdir Options
- Create Subdir: Create Subdirectory for the Windows destination.
- Create Subdir, option: Different parameters can be used to create the destination directory.
File Options
- Overwrite if file exists: Destination file will be overwritten.
- Only Newer Files: Only newer files will be processed to the destination.
- Skip if file exists: Skip if destination file already exists.
- Fail if file exists: Error if destination file already exists.
- Add version number suffix if file exists: Version number suffix will be added if destination file already exists (i.e. "filename.txt.1").
- Add version number (pre-ext) suffix if file exists: Version number (pre-ext) suffix will be added if destination file already exists (i.e. "filename.1.txt").
- Add version number prefix if file exists: Version number prefix will be added if destination file already exists (i.e. "1.filename.txt").
- Add date time sufffix if file exists: Date time suffix will be added if destination file already exists (i.e. "filename.txt.20131116114801"). Format date time used: "YYYYMMDDHHNNSS".
- Add date time (pre-ext) suffix if file exists: Date time (pre-ext) suffix will be added if destination file already exists (i.e. "filename.20131116114801.txt"). Format date time used: "YYYYMMDDHHNNSS".
- Add date time prefix if file exists: Date time prefix will be added if destination file already exists (i.e. "20131116114801.filename.txt"). Format date time used: "YYYYMMDDHHNNSS".
- Delete Extention: Delete the extention of the destination filename.
- Delete Prefix: Delete the prefix (see file prefix filter source option) of the destination filename.
- Reset Source File Archive Bit On Success (WIN as Source): On Windows when a file is created or modified, the archive bit is set, and when the file has been backed up, the archive bit is cleared. It is by use of the archive bit that incremental backups are implemented.
Rename Options
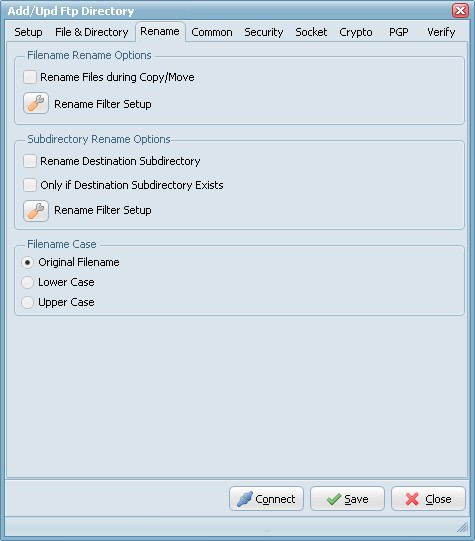
- Rename Files during Copy/Move: Use regular expressions to rename the destination filename. A very good site with information about regular expressions is http://www.regular-expressions.info/
- Rename Destination Subdirectory: Use regular expressions to rename the destination subdirectory.
- Only if Destination Subdirectory Exists: Rename only if destination subdirectory already exists.
- Filename Case: Use original filename, lower case or upper case for the destination filenames.
Common Options
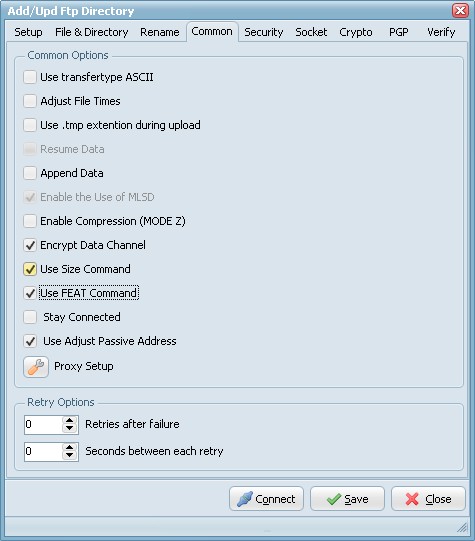
- Use transfertype ASCII: Use transfertype ASCII instead of Binary.
- Adjust File Times: File times will be adjusted after upload/download operation.
- Resume Data: When Resume contains True, the destination file will be opened and positioned to the end of the existing file data before retrieving new data.
- Append Data: When Append contains True, the FTP server will append data from the transfer to the end of a file which already exists on the FTP server.
- Enable Compression (MODE Z): Enable MODE Z Compression.
- Encrypt Data Channel: If this option is enabled the channel used for data transfer (files, directory listings) will be encrypted, otherwise only command channel will be encrypted.
- Use Size Command: Use this option to specify, whether SIZE command is sent when the data is downloaded. Use of this command lets the component report correct total size in OnProgress event, when the size of the data to be downloaded was not specified. Note, that some servers behave unexpectedly when SIZE command is used.
- Use FEAT Command: Use this option to specify, whether FEAT command is to be sent to the server. This command requests supported security mechanisms from FTPS server. Although server is not obliged to respond to it.
- Stay Connected: Don't disconnect the connection between scans.
- Use Adjust Passive Address: If this option is enabled, in passive mode data transfer, we will automatically set the address of the remote host to that from the control connection.
Proxy Settings
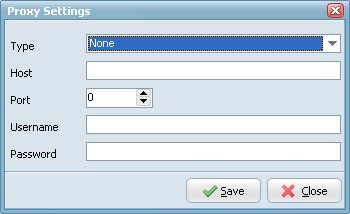
- Type: Use this option to specify type of the proxy server.
- no proxy
- user site proxy
- site proxy
- open proxy
- userpath proxy
- transparent proxy
- Host: Use this option to specify proxy server address.
- Port: Use this option to specify port on the proxy server.
- Username: Use this option to specify username.
- Password: Use this option to specify password.
Security Options
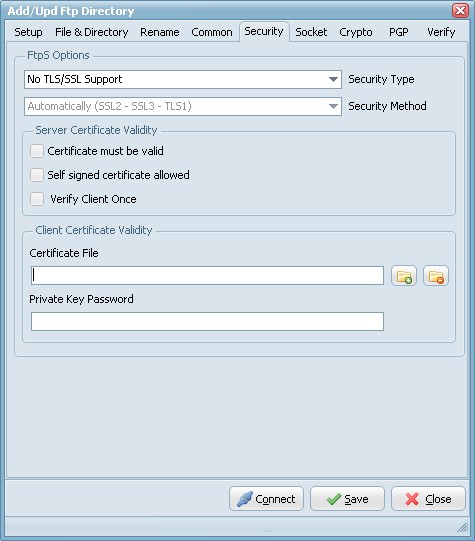
FTPS (also known as FTP Secure and FTP-SSL) is an extension to the commonly used File Transfer Protocol (FTP) that adds support for the Transport Layer Security (TLS) and the Secure Sockets Layer (SSL) cryptographic protocols.
FTPS should not be confused with the SSH File Transfer Protocol (SFTP), an incompatible secure file transfer subsystem for the Secure Shell (SSH) protocol. It is also different from Secure FTP, the practice of tunneling FTP through an SSH connection.
Security Type:
- Use Implicit TLS/SSL Support: Negotiation is not allowed with implicit FTPS configurations. A client is immediately expected to challenge the FTPS server with a TLS/SSL ClientHello message. If such a message is not received by the FTPS server, the server should drop the connection.
- Use Explicit TLS/SSL Support: In explicit mode (also known as FTPES), an FTPS client must "explicitly request" security from an FTPS server and then step-up to a mutually agreed encryption method. If a client does not request security, the FTPS server can either allow the client to continue insecure or refuse/limit the connection.
Security Method:
- Secure Sockets Layer SSLv2
- Secure Sockets Layer SSLv23
- Secure Sockets Layer SSLv3
- Transport Layer Security TLSv1
- Transport Layer Security TLSv1.1
- Transport Layer Security TLSv1.2
Server Certificate Validity
- Certificate must be valid: Certificate was validated successfully and is valid.
- Self signed certificate allowed: A self signed certificate is allowed.
- Verify client once:
Client Certificate Validity
- Certificate File: For authentication FTPS (or, to be more precise, SSL/TLS protocol under FTP) uses X.509 certificates.
- Private Key Password: Needed when your private key is encrypted with a passphrase.
Socket Options
Crypto Options
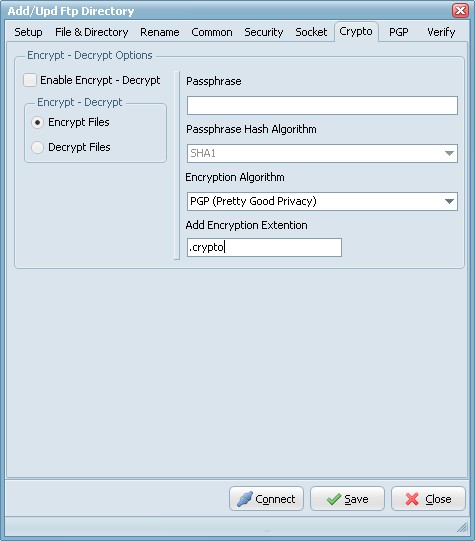
Encrypt - Decrypt Options
- Encryption & Decryption using the following Encryption algorithms: Blowfish, Cast 128, Cast 256, DES, 3DES, Ice, Thin Ice, Ice2, IDEA, Mars, Misty1, RC2, RC4, RC5, RC6, Rijndael (the new AES), Serpent, Tea, Twofish and PGP (Pretty Good Privacy). You can use the following Hash Algorithms for the password: Haval, MD4, MD5, RipeMD-128, RipeMD-160, SHA-1, SHA-256, SHA-384, SHA-512, Tiger. LimagitoX uses a 64 bit Salt. Salt = Random data that is included as part of a session key. When added to a session key, the plaintext salt data is placed in front of the encrypted key data. Salt values are added to increase the work required to mount a brute-force (dictionary) attack against data encrypted with a symmetric-key cipher.
- Encryption & Decryption available in Site and Corporate License. Encryption available in Lite and Single License.
PGP Options
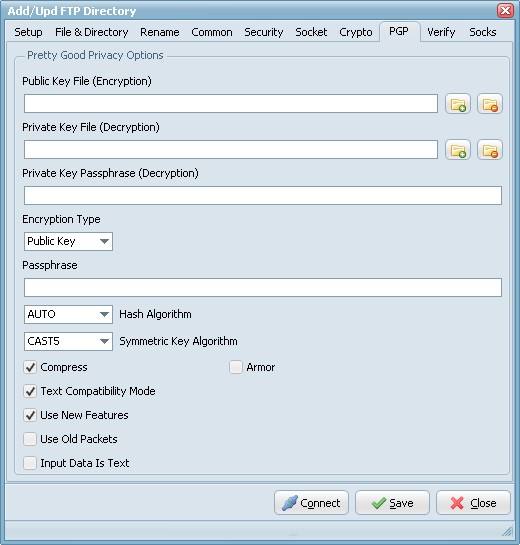
To enable PGP you need to set the Encryption Algorithm to PGP (check the Crypto Tab).
- Public Key File: Use this option to set the keyring with keys for data encryption.
- Private Key File: Use this option to determine keyring with keys for decryption.
- Private Key Passphrase: This option specifies password that will be used when trying to decrypt the private (secret) key used for file encryption.
- Encryption Type:
- Both: both public key and password will be used for encryption. It implies, that decryption can be performed by either the password or the private (secret) key.
- Passphrase: This property specifies the password that will be tried to use when decrypting the file, which was previously encrypted using symmetric algorithm (not with a public key).
- Hash Algorithm: Use this option to set algorithm that will be used for hash calculation.
- Symmetric Key Algorithm: Specifies the symmetric algorithm for data encryption.
- Compress: Data will be compressed before encryption.
- Text Compatibility Mode: Several versions of PGP have bug in their implementations that results in creation of incorrect text signatures. The following paragraph is taken from RFC 2440: «PGP 2.6.X and 5.0 do not trim trailing whitespace from a "canonical text" signature. They only remove it from cleartext signatures. These signatures are not OpenPGP compliant -- OpenPGP requires trimming the whitespace. If you wish to interoperate with PGP 2.6.X or PGP 5, you may wish to accept these non-compliant signatures.» One can say that this bug also exists in PGP6.5 and PGP8.0 implementations. It is a good idea to enable this property if you want to interoperate with those versions of PGP. Disable this option if you need to create OpenPGP-compliant messages.
- Use New Features: Use this optiony for compatibility with old versions of PGP-compatible software. If this option is enabled, then newer and stronger algorithms will be used. In this case ClearTextSign andSign will be compatible with PGP 2.6.x, while Encrypt and EncryptAndSign will not. If the option is disabled, then the result will be compatible with PGP 2.6.x, while the keys are compatible (i.e. don't use features not supported by PGP 2.6.x).
- Use Old Packets: If this option is enabled only packets of old format will be used in order for compatibility with PGP 2.6.x.
- Input Is Text: Use this option when you want to specify that input data must be interpreted as text.
- Armor: Use this option to determine if resulting data should be armored, i.e. wrapped into base64-cover. ASCII armor is a binary-to-textual encoding converter. ASCII armor is a feature of a type of encryption called pretty good privacy (PGP). ASCII armor involves encasing encrypted messaging in ASCII so that they can be sent in a standard messaging format such as email.
Verify Options
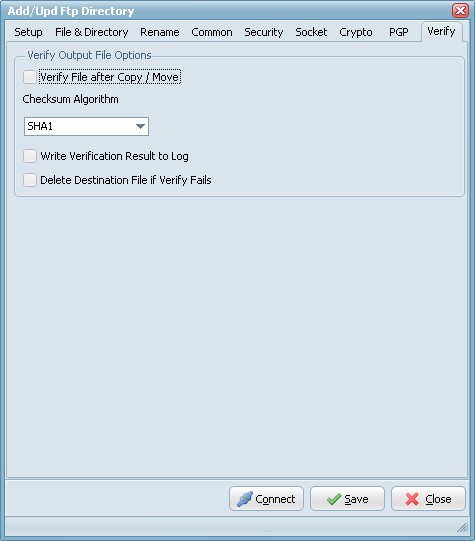
Verify File Options
- Verify File after Copy/Move: Compares source and destination file for verified transfer integrity.
- Checksum Algorithm: Checksum Algorithm used for verified transfer integrity. Automatic: select the algorithm using the following preferred order: 1. SHA1, 2. MD5, 3. CRC32
- Write Checksum result to Log: Checksum result will be written into the Log file.
- Delete Destination File if Verify Fail: Destination file will be deleted if verification fails.
Socks Options
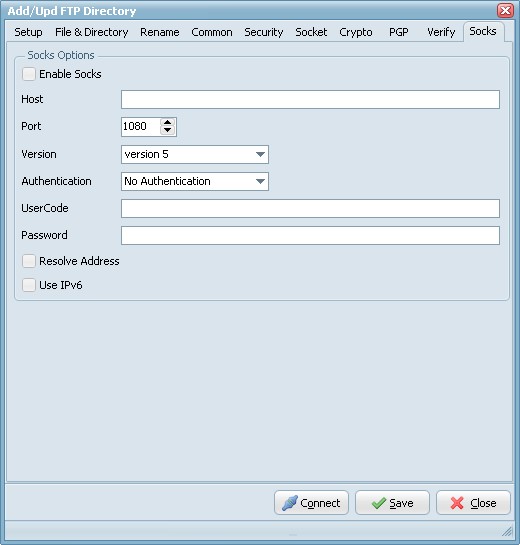
- Enable Socks: This option defines whether the connection is established directly (Enable Socks is disabled) or via SOCKS server (Enable Socks is enabled).
- Host: This property specifies the IP address or host name of the SOCKS server.
- Port: Specifies the port that SOCKS server is bound to. Default value is 1080.
- Version: This option specifies the version of SOCKS protocol to be used with the SOCKS server. Default value is version 5.
- Authentication: This option specifies the method of authentication to use with the SOCKS server. The methods supported are "No Authenticate" and "UserCode".
- UserCode: This property specifies the user code (username) to access the SOCKS server.
- Password: This property specifies the password to access the SOCKS server.
- Resolve Address: Specifies whether the address of destination host is resolved or passed to SOCKS server for resolving. Usually the host name is resolved on the client system. However some policy can forbid DNS operations on client computers. Then the client needs to pass the host name to the SOCKS server unresolved (SOCKS server is supposed to resolve it itself).
- Use IPv6: This option defines whether IP protocol version 6 should be used.
Copyright © 2007-2013, www.limagito.com












