SMTP Destination
SMTP Destination Setup
Setup Options
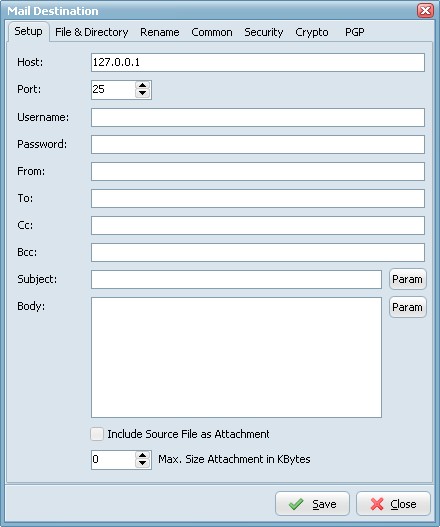
- Host: This option specifies the address of the host to connect to.
- Username: Authentication identity used when in to the server.
- Password: Authentication credentials used when logging into the server.
- Port: Port number on the host to connect to (Default value is 25).
- From: Identifies the original author of the message.
- To: Identifies the recipients of a message.
- CC: Carbon copy recipients for the message.
- BCC: Indicates blind carbon copy recipients for the message.
- Subject: Identifies the subject for the message.
- Body: Represents the body of the message.
- Include Input File as Attachment: Source file will be included as attachment.
- Max. Size Attachment in Kbytes: Maximum size attachment in Kbytes (Default value is zero = Unlimited).
File & Directory Options
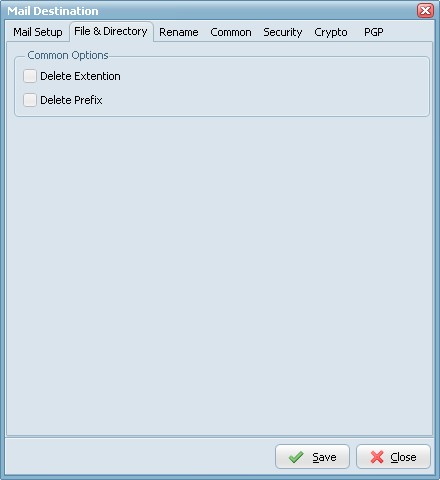
- Delete Extention: Delete the extention of the destination filename.
- Delete Prefix: Delete the prefix (see file prefix filter source option) of the destination filename.
Rename Options
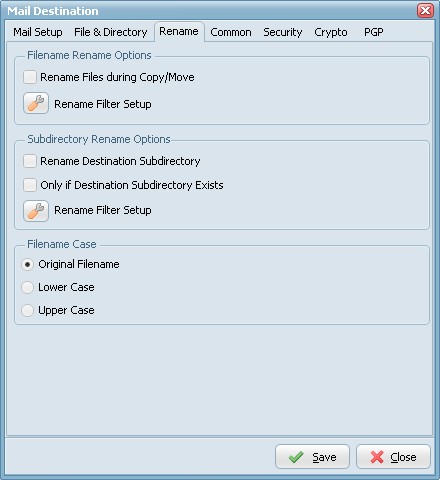
- Rename Files during Copy/Move: Use regular expressions to rename the destination filename. A very good site with information about regular expressions is http://www.regular-expressions.info/
- Rename Destination Subdirectory: Use regular expressions to rename the destination subdirectory.
- Only if Destination Subdirectory Exists: Rename only if destination subdirectory already exists.
- Filename Case: Use original filename, lower case or upper case for the destination filenames.
Common Options
Security Options
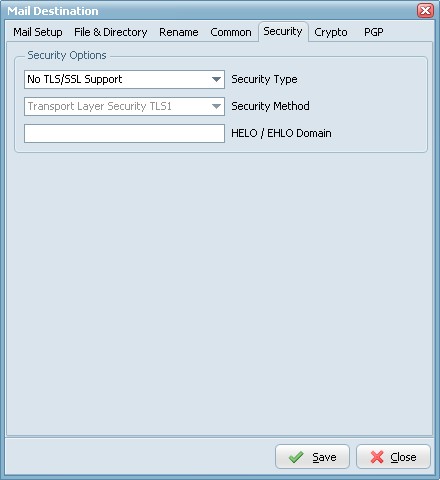
- With the security options you can enable TLS/SSL support.
- HELO/EHLO Domain: Ask the server for the SMTP extensions that the server supports, by using the EHLO greeting of the Extended SMTP specification (RFC 1870). Fall back to HELO only if the server does not respond to EHLO.
Crypto Options
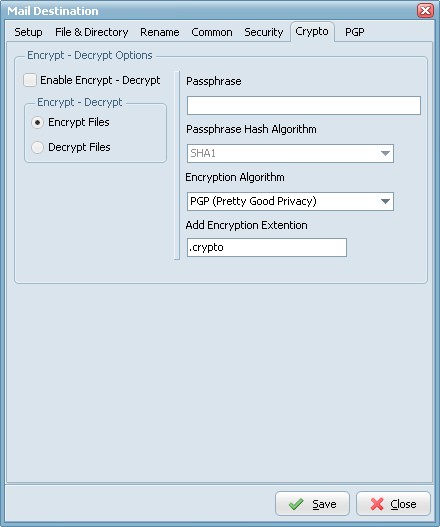
Encrypt - Decrypt Options
- Encryption & Decryption using the following Encryption algorithms: Blowfish, Cast 128, Cast 256, DES, 3DES, Ice, Thin Ice, Ice2, IDEA, Mars, Misty1, RC2, RC4, RC5, RC6, Rijndael (the new AES), Serpent, Tea, Twofish and PGP (Pretty Good Privacy). You can use the following Hash Algorithms for the password: Haval, MD4, MD5, RipeMD-128, RipeMD-160, SHA-1, SHA-256, SHA-384, SHA-512, Tiger. LimagitoX uses a 64 bit Salt. Salt = Random data that is included as part of a session key. When added to a session key, the plaintext salt data is placed in front of the encrypted key data. Salt values are added to increase the work required to mount a brute-force (dictionary) attack against data encrypted with a symmetric-key cipher.
- Encryption & Decryption available in Site and Corporate License. Encryption available in Lite and Single License.
PGP Options
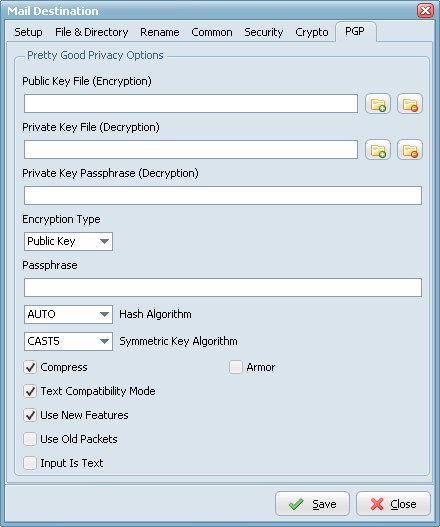
To enable PGP you need to set the Encryption Algorithm to PGP (check the Crypto Tab).
- Public Key File: Use this option to set the keyring with keys for data encryption.
- Private Key File: Use this option to determine keyring with keys for decryption.
- Private Key Passphrase: This option specifies password that will be used when trying to decrypt the private (secret) key used for file encryption.
- Encryption Type:
- Both: both public key and password will be used for encryption. It implies, that decryption can be performed by either the password or the private (secret) key.
- Passphrase: This property specifies the password that will be tried to use when decrypting the file, which was previously encrypted using symmetric algorithm (not with a public key).
- Hash Algorithm: Use this option to set algorithm that will be used for hash calculation.
- Symmetric Key Algorithm: Specifies the symmetric algorithm for data encryption.
- Compress: Data will be compressed before encryption.
- Text Compatibility Mode: Several versions of PGP have bug in their implementations that results in creation of incorrect text signatures. The following paragraph is taken from RFC 2440: «PGP 2.6.X and 5.0 do not trim trailing whitespace from a "canonical text" signature. They only remove it from cleartext signatures. These signatures are not OpenPGP compliant -- OpenPGP requires trimming the whitespace. If you wish to interoperate with PGP 2.6.X or PGP 5, you may wish to accept these non-compliant signatures.» One can say that this bug also exists in PGP6.5 and PGP8.0 implementations. It is a good idea to enable this property if you want to interoperate with those versions of PGP. Disable this option if you need to create OpenPGP-compliant messages.
- Use New Features: Use this optiony for compatibility with old versions of PGP-compatible software. If this option is enabled, then newer and stronger algorithms will be used. In this case ClearTextSign andSign will be compatible with PGP 2.6.x, while Encrypt and EncryptAndSign will not. If the option is disabled, then the result will be compatible with PGP 2.6.x, while the keys are compatible (i.e. don't use features not supported by PGP 2.6.x).
- Use Old Packets: If this option is enabled only packets of old format will be used in order for compatibility with PGP 2.6.x.
- Input Is Text: Use this option when you want to specify that input data must be interpreted as text.
- Armor: Use this option to determine if resulting data should be armored, i.e. wrapped into base64-cover. ASCII armor is a binary-to-textual encoding converter. ASCII armor is a feature of a type of encryption called pretty good privacy (PGP). ASCII armor involves encasing encrypted messaging in ASCII so that they can be sent in a standard messaging format such as email.
Copyright © 2007-2013, www.limagito.com







