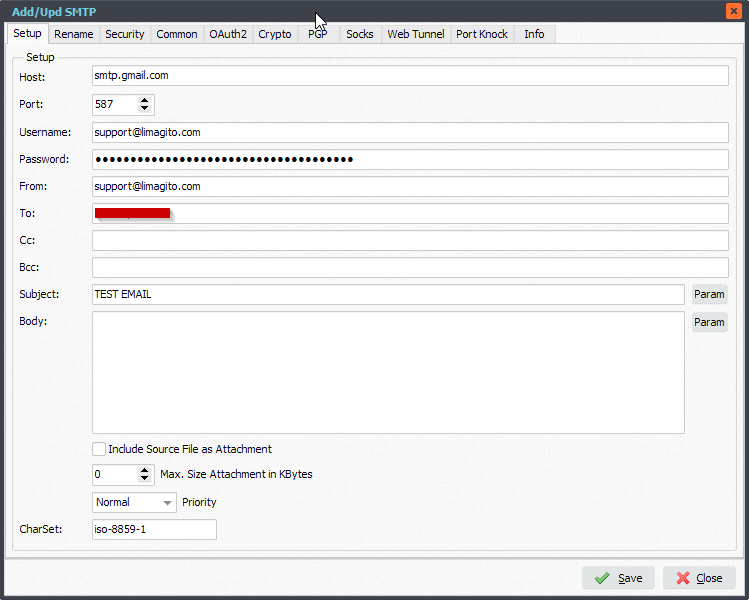
Q: Sending emails using GMail SMTP with OAuth2 authentication. I am trying to set up an outgoing email notification that will happen when a file moves to it’s destination.
8th of May 2022, we are working on an update because of: OAuth out-of-band (oob) flow will be deprecated
Instead of the Google URI urn:ietf:wg:oauth:2.0:oob you’ll have to use a loopback (IP) address as Redirect URI like http://127.0.0.1 or http://localhost
Starting from version v2022.5.8.0 a redirect port will be added to the OAuth2 setup which is only needed during the OAuth2 verification setup.
A: Yes this is possible.
First check if you enabled the GMail API in your account: https://support.google.com/googleapi/answer/6158841?hl=en
Secondly we’ll need credentials ‘Client ID and Client Secret’ for the OAuth2 authentication: https://support.google.com/googleapi/answer/6158857?hl=en&ref_topic=7013279
We added some screenshots to help you with the setup.
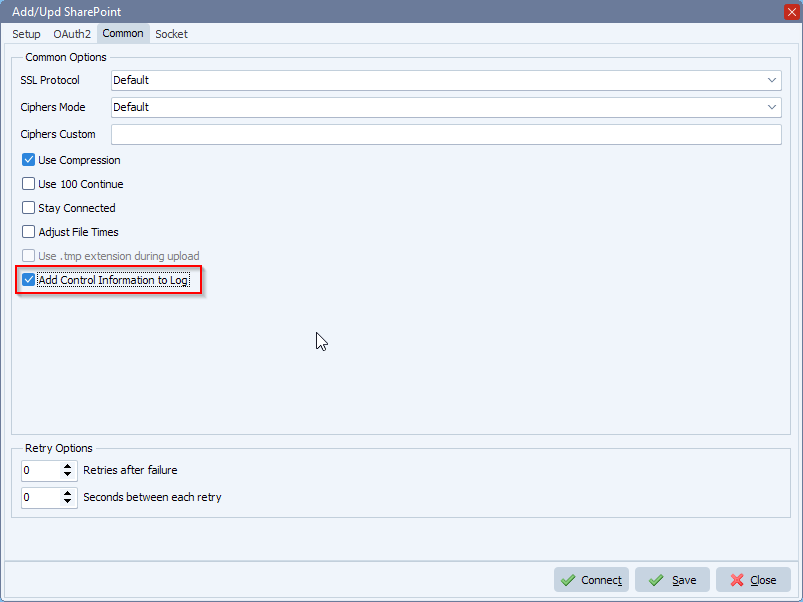
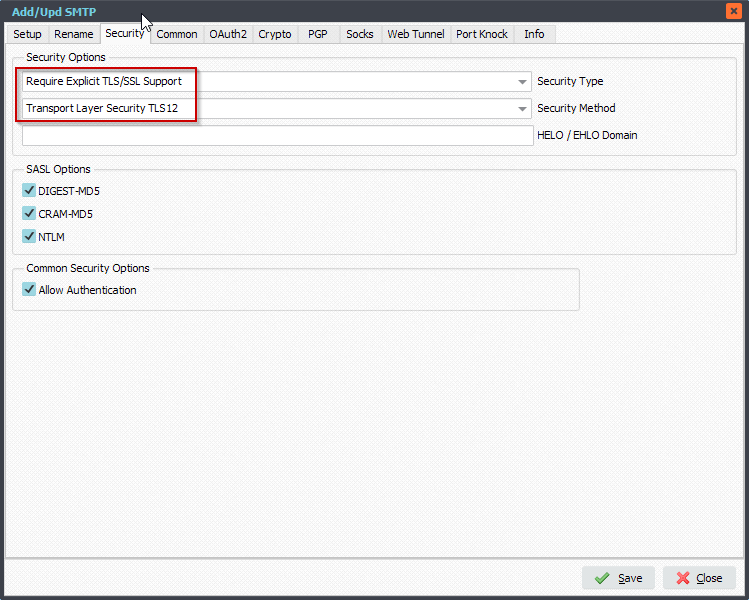
Don’t forget the Security Options:
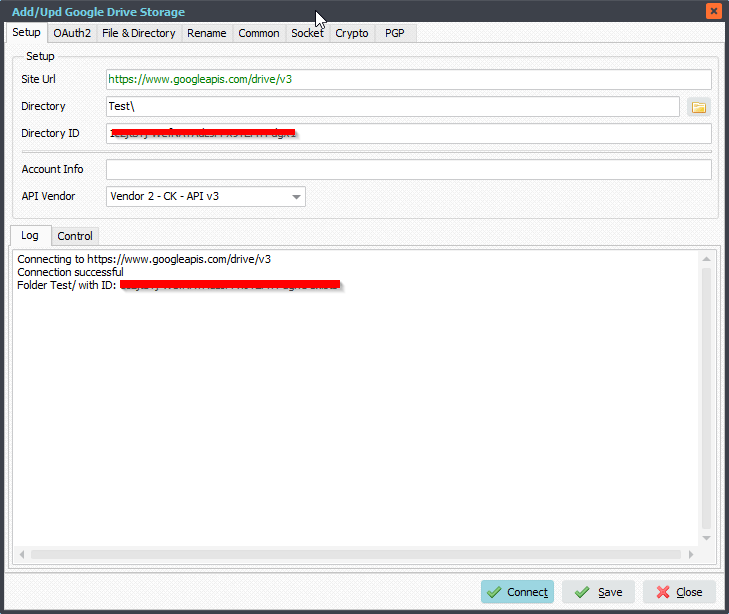
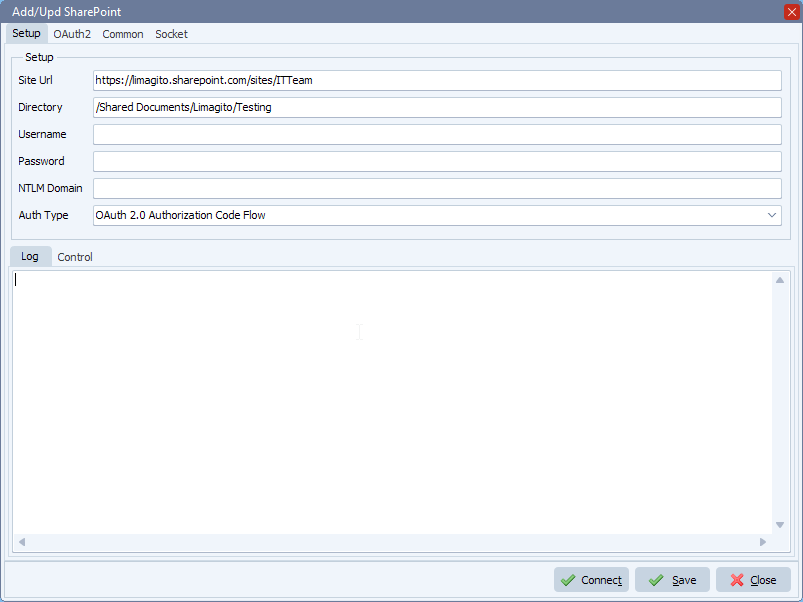
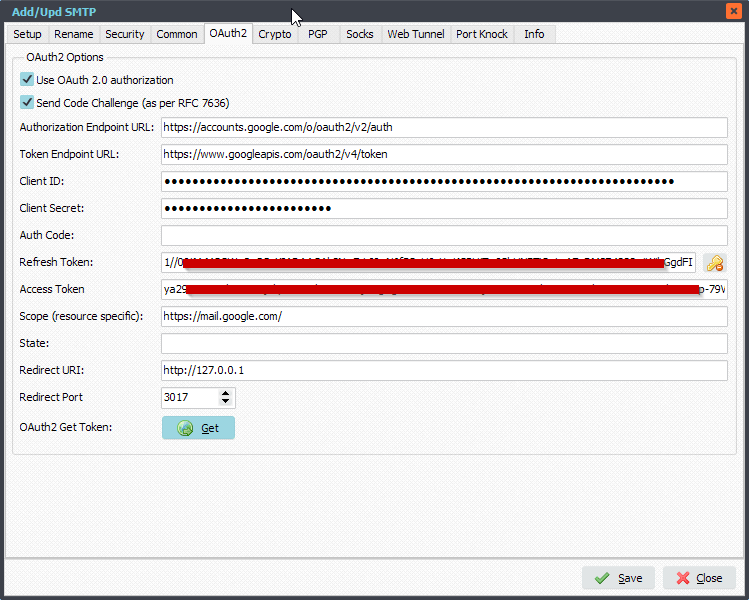
OAuth2 Setup:
Please add the following information:
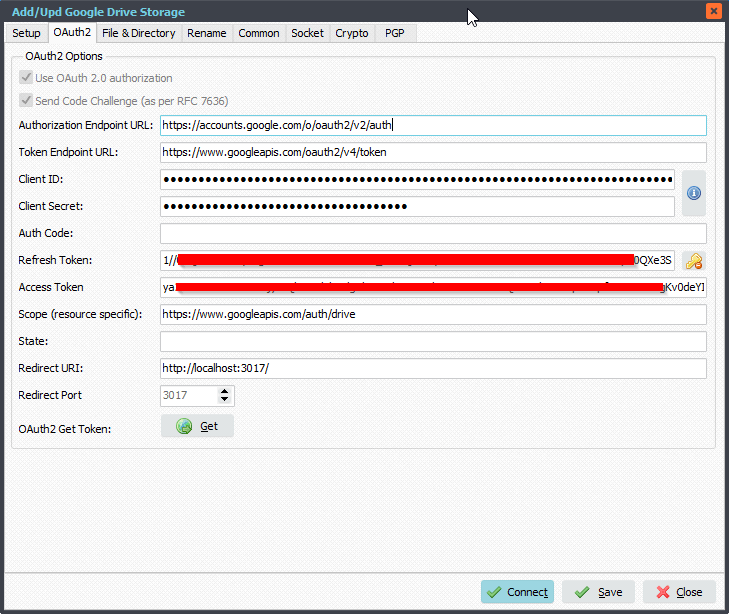
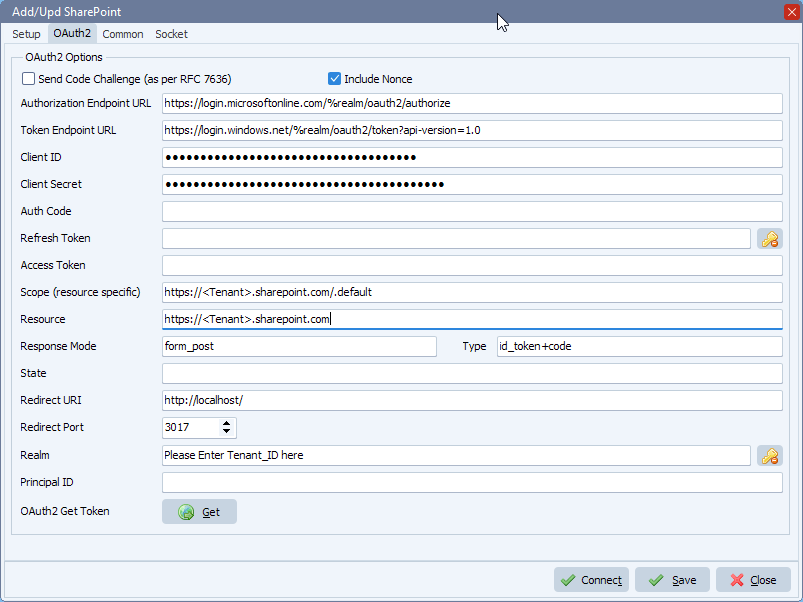
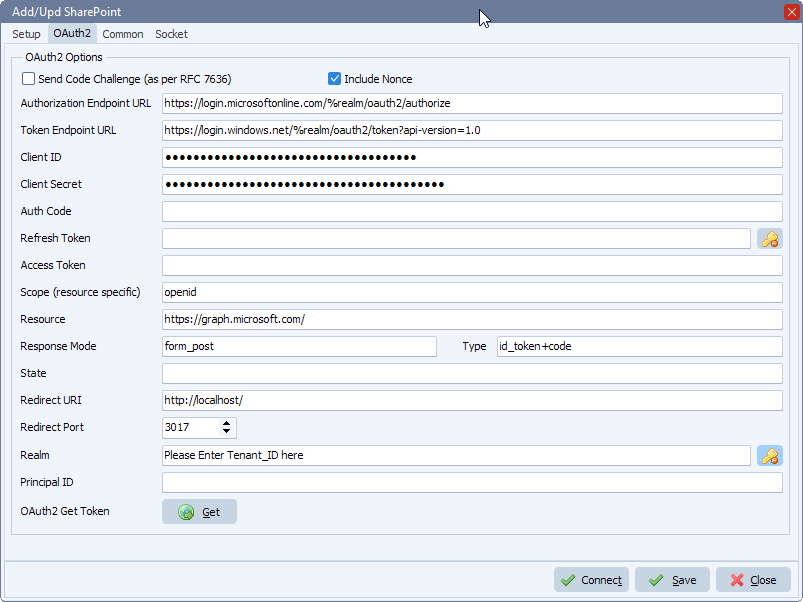
– Authorization Endpoint URL: https://accounts.google.com/o/oauth2/v2/auth
– Token Endpoint URL: https://www.googleapis.com/oauth2/v4/token
– Client ID
– Client Secret
– Scope: https://mail.google.com/
– Redirect URI: http://127.0.0.1
– Redirect Port: 3017 (can be any other port that is not in use)
Click GET and your browser will open. Please follow the steps in your browser and after acceptance we will automatically fill in Refresh Token and Access Token. Do not forget to <Save> afterwards.
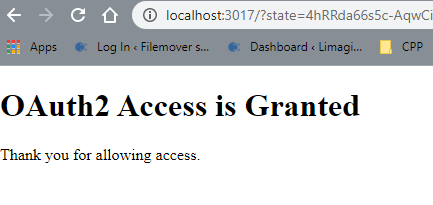
RunTime Log Result when testing:
8/05/2022 17:54:07 OAuth2 Authorization Successful
8/05/2022 17:54:09 Send Success C:\Test\In\IntroXFM.pdf to smtp.gmail.com;1356113
8/05/2022 17:54:09 ************************************************************
8/05/2022 17:54:09 Rule Start Time: 8/05/2022 17:54:07
8/05/2022 17:54:09 Rule End Time: 8/05/2022 17:54:09
8/05/2022 17:54:09 Total Files Successful, Count: 1 & Size: 1356113
8/05/2022 17:54:09 ************************************************************
#FileTransfer
If you need any
info about this ‘GMail SMTP with OAuth2’ question, please let us know.
Best regards,
Limagito Team