Q: I am asked to provide a public SSH key for the new connection.
>> Are you able to provide me a public ssh key so we can make the connection passwordless? Let me know and I will create the account so you can test your connection. Thanks
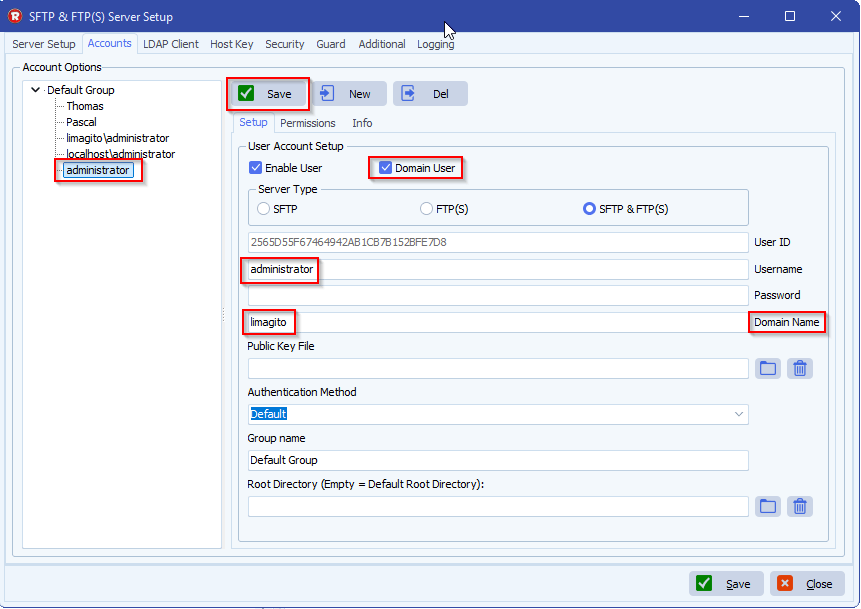
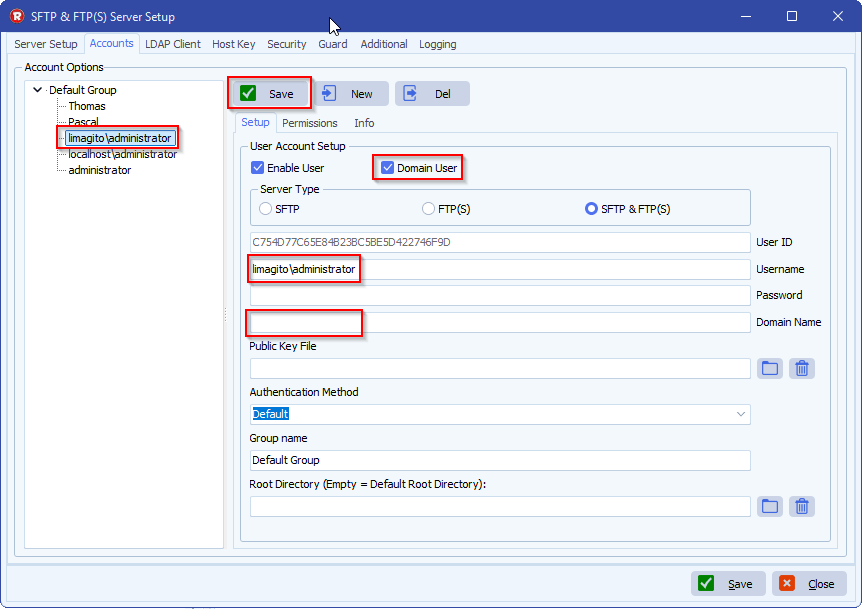
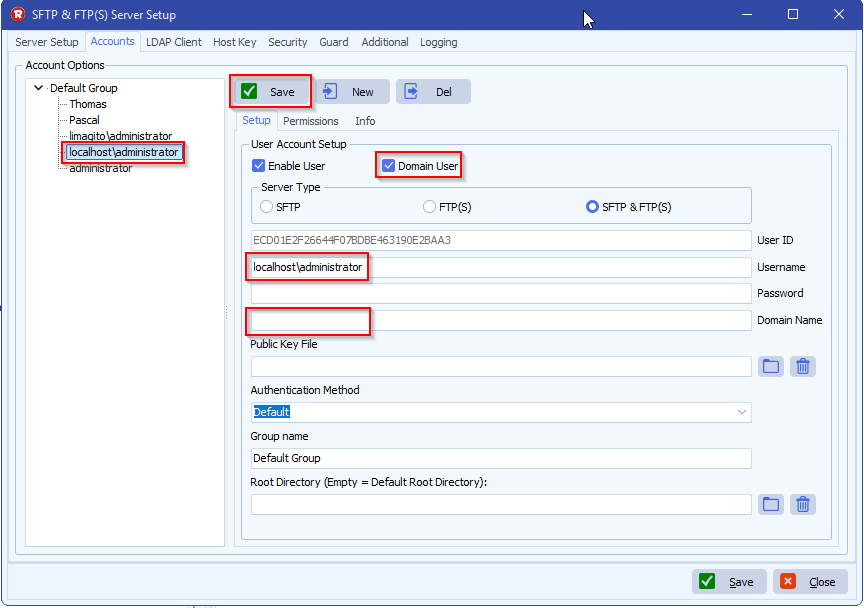
Can I give them the same public key I use for encrypting files, and set up on my rule same as I have set up to decrypt files with the private key and password? See the screen shot below.
If you can let me know as soon as possible, I would greatly appreciate it. Thank you.
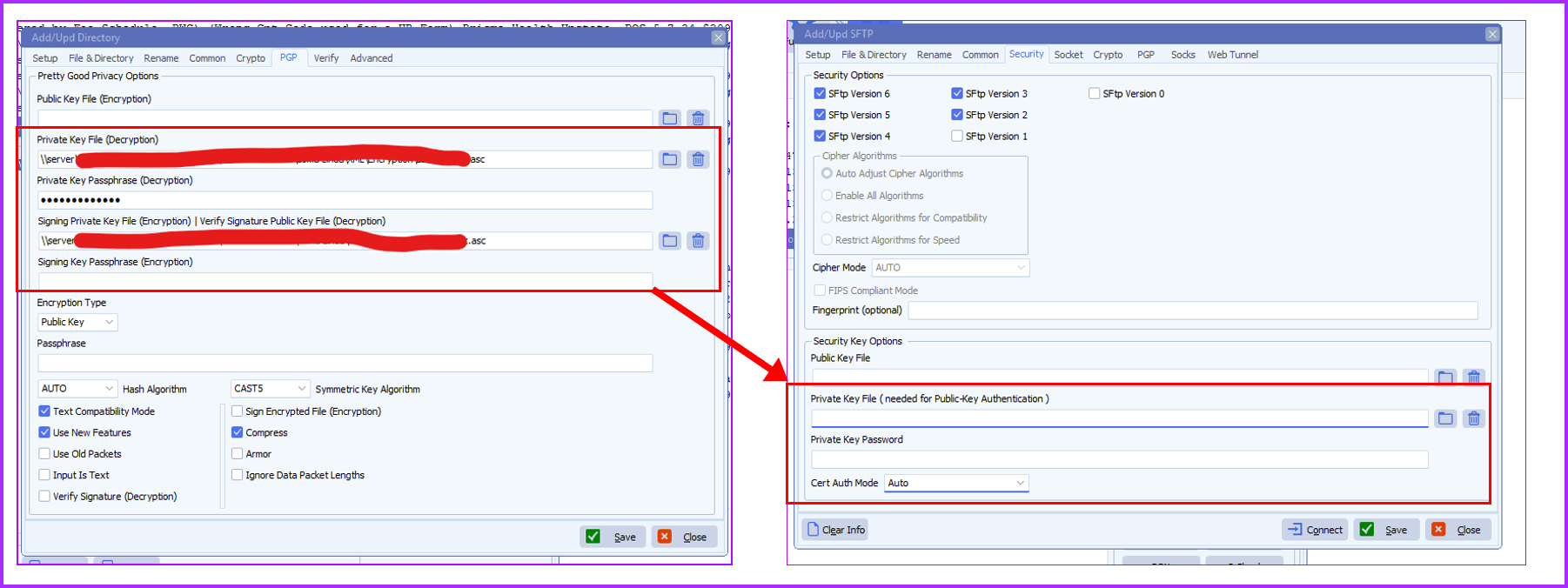
A: No, you can not use PGP encryption/decryption keys for SFTP Public-Key authentication
https://limagito.com/how-to-
If you need any help with this new option, please let us know.
Best Regards,
Limagito Team
#SFTP #SSH #managedfiletransfer #filetransfer #filemanagement