The SSH Terrapin Attack
In Limagito File Mover v2024.2.3.0 we made some changes to mitigate the SSH Terrapin attack problem. We did this by modifying the selection of the default algorithms in the following ways:
- chacha20-poly1305@openssh.com is no longer included by default. It can be re-added by specifying “+chacha20-poly1305@openssh.com” in the new UncommonOptions property we added.
- We kept the “-cbc” encryption modes because potentially too many servers would be affected by eliminating these encryption algorithms.
- We no longer include the “-etm” MAC algorithms, which are:
- hmac-sha1-etm@openssh.com
- hmac-sha2-256-etm@openssh.com
- hmac-sha2-512-etm@openssh.com
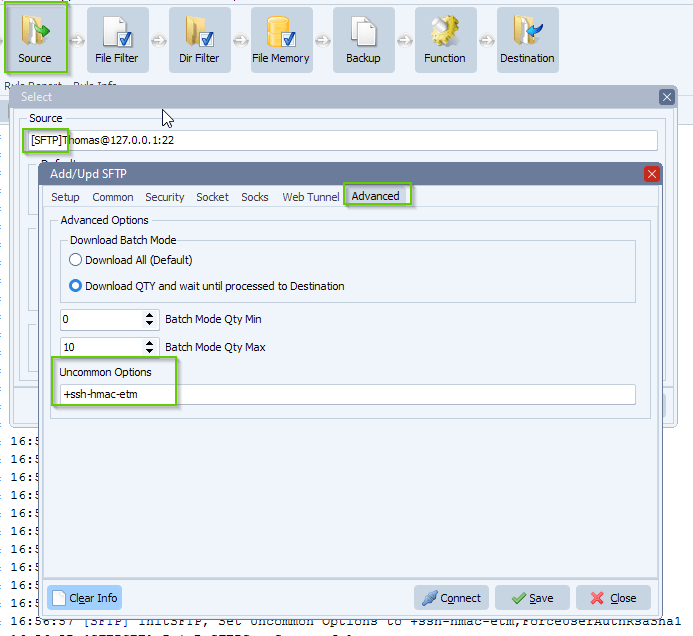
The -etm MAC algorithms can be re-added by specifying “+ssh-hmac-etm” in the new UncommonOptions property.
For more information about the Terrapin attack, see https://terrapin-attack.com/
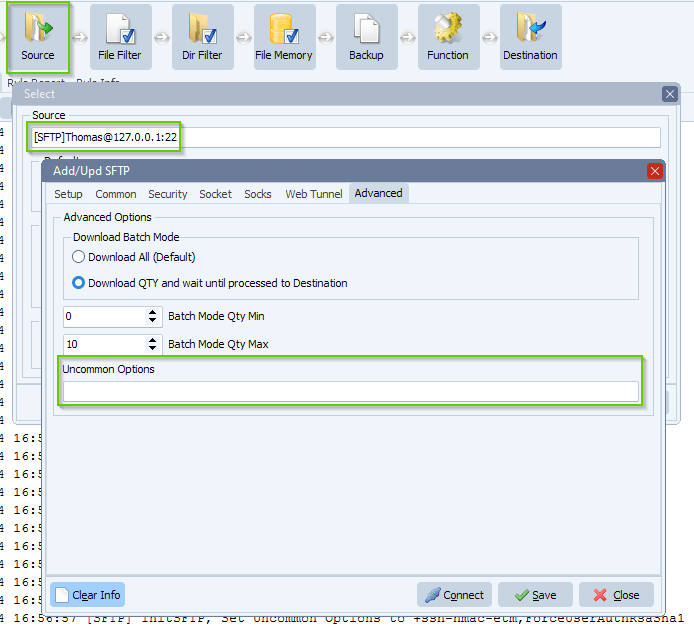
- In the following example I re-added the -etm MAC algorithms by specifying “+ssh-hmac-etm” in the new “Uncommon Options” property (Advanced Tab).
#sftp #ssh #managedfiletransfer #filetransfer #filemanagement
If you need any help with this ‘Terrapin Attack’, please let us know.
Best Regards,
Limagito Team
