In version 2020.2.28.0 we added an option called ‘Common Parameters’. The goal of this option is to make it easier for you to use common configuration items throughout your Moving Rules. We’ve added some screenshots to make it more clear.
> Common Parameters Setup can be found under the Common menu item.
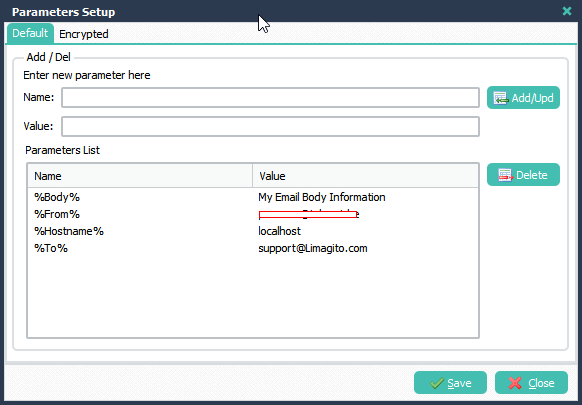
> In the screenshot below you can see that we’ve added 4 of them:
- %Body%
- %From%
- %Hostname%
- %To%
All “Common Parameters” must start & end with a % sign.
> We’ll be using these Common Parameters within the Mail Event Setup of different Moving Rules.
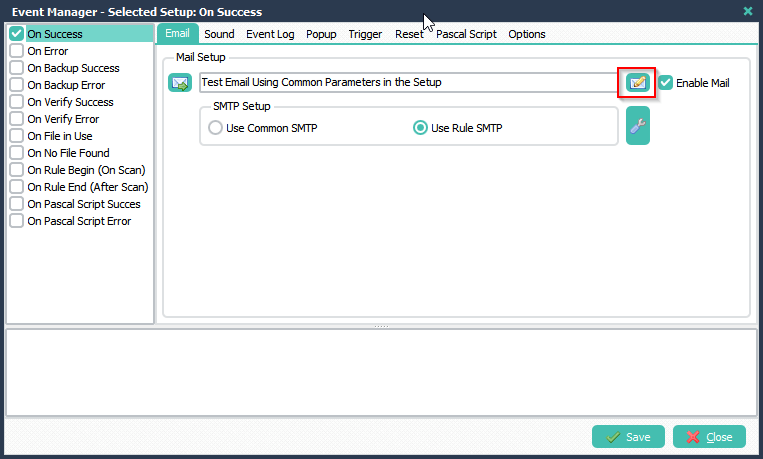
> Added %From, %To% and %Body% to the Email Setup.
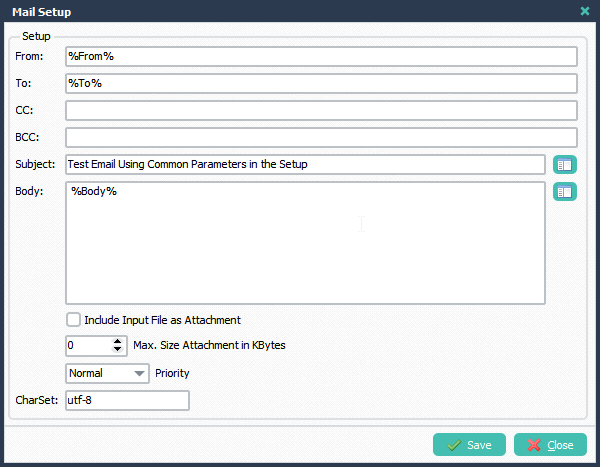
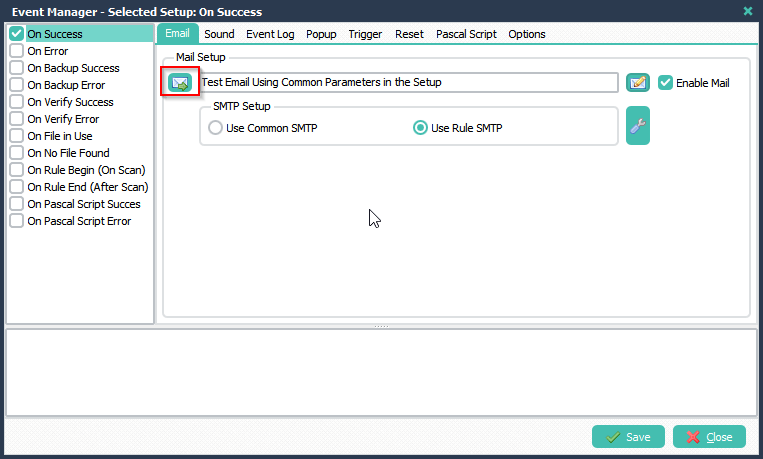
> Finally we’ll send a test email ..
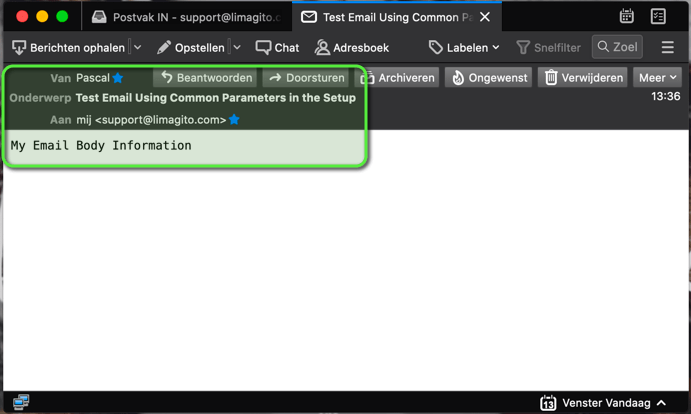
If you want to use a “Common Parameter” in a certain setup field where it does not work yet, please let us know. We’ll add this asap.
If you need any help, please let us know.
Regards,
Limagito Team